Project Stories
Get your project on board

Ensure Your Peace of Mind - Stay Ahead with Our Reliable Monitoring Service! Don't wait for downtime to disrupt your business. Take charge with our proactive monitoring solution. Sign up Free now and rest assured knowing your website or service is in safe hands! Here
Our website monitoring service ensures your site stays online and running smoothly. Get alerted to any downtime or issues in real-time, so you can focus on growing your business.

Web Site and Online Service Monitor and Alert System Under Development
In today's fast-paced digital world, businesses rely heavily on their website and online services to connect with their customers. A website is often the first point of contact for potential customers, and an online service can be the backbone of a business's operations. Therefore, it is essential to ensure that these digital assets are always up and running smoothly.
To achieve this, businesses often employ a web site and online service monitor and alert system. This system continuously checks the website and online services, looking for any issues or downtime. If any issues are detected, the system alerts the business's IT team, allowing them to quickly address the problem and minimize downtime.
While many companies choose to develop their own monitoring and alert systems, there are several benefits to using third-party services. One such benefit is the ability to receive alerts on mobile devices. With a third-party system, alerts can be sent directly to a mobile phone, allowing IT teams to quickly respond to any issues, even if they are away from their desks.
Additionally, third-party systems often provide real-time monitoring and status updates for a wide range of services and applications. This can be especially useful for businesses that rely on multiple online services and applications. Having a single dashboard to view the status of all these services can save IT teams a significant amount of time and effort.
Perhaps the most significant benefit of a web site and online service monitor and alert system is the ability to know about any issues before your customers do. Downtime or issues with a website or online service can negatively impact a business's reputation and lead to lost revenue. By being alerted to any issues immediately, businesses can quickly address the problem and minimize the impact on their customers.

In conclusion, a web site and online service monitor and alert system is a vital tool for any business that relies on its website and online services. While developing an in-house system is an option, there are several benefits to using a third-party service, including mobile alerts and real-time monitoring. By knowing about any issues before their customers do, businesses can maintain their reputation and minimize the impact of downtime or issues with their digital assets.
AI Tools and Services

With AI moving faster than you read, we help business solve real problems, add AI where it makes sence, and solve problems created by bad AI implementations.
A List of available tools:
Document NFT

Document Management on the blockchain. NFT is for images and other media assets, DNFT is for documents, Share documents with others, secure documents for permanent storage!
All in 1 place,Save all your Documents and Contracts, signed and original, use the DNFT Explorer to search, sign, upload, share and market your templates to others.
Utilizing the Blockchain for Document Storage
Blockchain technology can be employed to store documents or document hashes and offers a number of benefits, including easy authentication and tamper-proof protection. Our blog post from 2019, titled "Document Signing and Validation Using Blockchain", outlines how to store each signed document on its own blockchain.
Tamper Resitant
Tamper resistance is a feature that is designed to protect against malicious attempts to modify or disable a system or program. It is a measure of the system's ability to withstand attempts to make unauthorized changes or gain access to sensitive information.
A blockchain's blocks are connected cryptographically by the hashing of the previous block hash into the present block hash. This highly secure tamper resistance prevents document forgery and simplifies verification. Although it may be possible to store an entire document on a blockchain, file size constraints may impede this technique. Hashes are a more viable choice to store documents on a blockchain due to their decreased size. Every time a document is modified, the cryptographic hash also changes. With the block hash containing the document data, the blockchain can validate the document by verifying the integrity of the blockchain.
In this example, the hash of each block is generated through the process of hashing the components that follow
- Time of registering
- Hash of the prior block
- Information (our document identification hash)
- Number used only once
Simple workflow as show here:
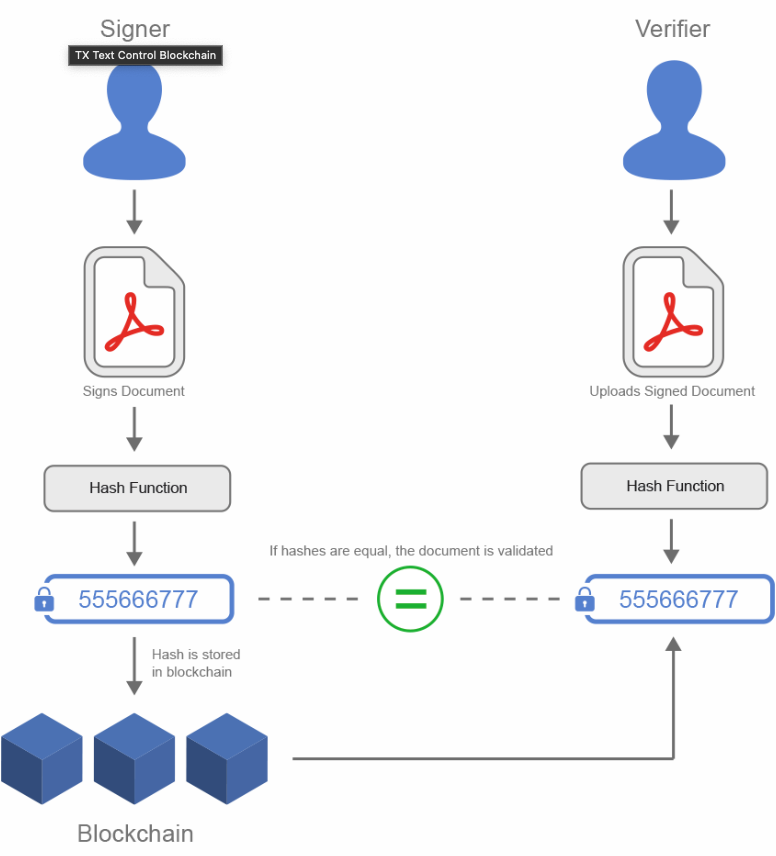
Putting away for Safekeeping
The BlockHash is produced from the PreviousBlockHash, the timestamp, and the Data that is present within each block. Every block has both the PreviousBlockHash and the Data in it.
Verification of Documents
Once a document has been uploaded and linked, the newly generated PDF can be confirmed by submitting it for comparison and if the hash codes match, it is genuine copy of the original uploaded file.
Summary
In conclusion, it can be determined that...
The latest version of any uploaded or signed document can be authenticated by using a blockchain to store the document's hash. The blockchain will always hold the information regarding the current version of the specified document.

True blockchain for business, Distributed technology to solve real business problems!
Security you need
Securing your online presence is more important now than ever, any breech can devastate your business, and any help, guidance or even a security audit to highlight potential risk's is important, knowledge is power. We can help you, but as a start, follow our Ten point guide below.

Guidelines to Enhance Data Protection
On a daily basis, news about security breaches in prestigious companies worldwide are being reported. This shows how delicate data can be and how many businesses do not have sound security systems in place. Keeping your data secure is paramount to the successful operation of your company. Your trade secrets, financial information and employee data must be secured. If it is compromised, it can lead to adverse effects on your reputation and financial losses. To ensure you don't become a headline, there are steps that can be taken.
1. Secure the information itself, not just the boundaries
The majority of security budgets are spent on firewall technology, but there exist numerous ways to get around these walls. Customers, suppliers, and staff are able to gain access to data outside of cyber-security protocols and misuse confidential information. To strengthen security, it is essential to focus on the data itself, not just the perimeter.
2. Be mindful of threats from within
It's easy to focus on external threats, as these are often the ones we hear about in the media. However, it is often overlooked that it's your insiders that can cause the most damage. Insider attacks can be very hard to identify and stop. An example of this is an employee clicking on a malicious email attachment they think is from a reliable source, which can lead to a ransomware worm being released. These types of threats are quite common and can be very costly.
3. Secure all devices by encryption
Nowadays, a growing number of people are selecting to carry out their work on their individual mobile gadgets. What can be done to guarantee these gadgets are reliable? Encrypt all data and ensure the encryption remains intact during transfers.
4. Examining your security measures
Do not be deceived into thinking that just because you have an antivirus on all of your company's computers and devices that you are immune to attack. Recent data breaches have made it clear that having a professional organization review your security measures is essential; a security audit will inevitably show up weaknesses you were not aware of. I suggest that you take a tour of the office and take a closer look at your employees' workstations. I assure you that if you look carefully, you will find a password written down on a sticky note.
5. Remove any unnecessary data
Organizations that handle confidential information, such as those in healthcare, finance, the public sector and education, need to put mechanisms in place for disposing of this data. This helps stop forgotten or neglected data from being pilfered at a later point in time. Implementing a system for shredding, wiping, or transforming redundant data to be illegible is an effective way to guarantee that your personnel do not store it.
6. Investing additional resources into Cyber-security both financially and with time
It is widely accepted that investing both time and money into data security is essential, as the potential danger of not doing so is the biggest threat to any IT infrastructure. To safeguard their confidential business information, numerous large organizations have appointed Chief Security Officers to board-level roles, to make sure that cybersecurity is included in all their business operations.
7. Create passwords that are hard to guess
Organizations often still maintain lenient password policies, resulting in simple, generic passwords that are easily cracked into. To improve security, the first move is to establish strong passwords. They should be complex enough, and changed every 90 days. Avoid using passwords such as "12345" or "Admin1" and keep them safe by not writing them down and leaving them in plain view.
8. Keep your applications up-to-date
It is important to keep your computer up to date with the latest patches and updates to ensure it is secure. The effectiveness of your security software depends on how recently it has been updated. Cyber criminals and malware are consistently finding new ways to exploit any flaws in older versions of software, so it is smart to check for updates frequently.
9. Make sure to have regular backups of your data
Having secure backups should be a fundamental element of any IT security plan. This will ensure that you can endure anything from the unintentional deletion of files to a total ransomware shutdown. As a security standard, the backup data should be kept in a safe and distant spot other than the main office.
10. Establish a corporate attitude that focuses on security
It is the responsibility of all those with a username and password to ensure data security. IT administrators should take the time to remind their staff and supervisors that logon information should not be shared with anyone outside of the organization. Data security is not just the responsibility of the IT team, but rather it is the job of all members of the company.

Cat Stories

Our cat diaries video series is available on youtube, some of the videos are linked below:
The Stars are Sooty and Sweep, Sweep is the Boss, or the smarter one, all black Bombay. Sooty thinks he is the boss, the older of the 2 by 5 years.
Our most poluar story for Halloween!
Commedy Club event
Original Christmas Song
Subscribe to the channel, and add comments, more will come, and requests are welcome. The tools I use are
- Realusion Labs Animation studio.
- Davinci Resolve Video Editing
- Audacity for Audio manipulation
- Personal creativity for the stories
- Occasional Fiver gigs for Singers!
Thanks for passing by
Your Next Project?
Let's Collaborate: Why Sharing Your Business Ideas is a Smart Move
As a business owner, you're always looking for ways to improve and grow your company. But what if we told you that sharing your ideas with others could be the key to unlocking your company's full potential? By collaborating with experts in the tech industry, you can leverage their technical skills to bring your ideas to life and take your business to new heights.
At our tech firm, we understand that businesses are often hesitant to share their ideas with outsiders. But we believe that the benefits of collaboration far outweigh the risks. When you share your ideas with us, we can provide you with fresh perspectives, technical expertise, and access to cutting-edge tools and resources that you might not have on your own.
One of the biggest advantages of collaborating with us is that we can help you develop a customized solution that meets your unique business needs. We understand that every business is different, and we take the time to get to know your company and its goals before we start working on a project. This ensures that the end product is tailored to your specific requirements and provides maximum value to your business.
Another advantage of collaborating with us is that we can help you stay ahead of the curve when it comes to emerging technologies. We're constantly researching and experimenting with new technologies and techniques, and we can bring that knowledge to your project. This means that you can stay ahead of your competitors and be well-positioned to take advantage of new opportunities as they arise.
Finally, collaborating with us can help you save time and money. Developing a new technology solution from scratch can be a time-consuming and expensive process. But by working with us, you can leverage our existing expertise and resources to accelerate the development process and reduce the overall cost of the project.
In conclusion, sharing your ideas with experts in the tech industry can be a smart move for your business. By collaborating with us, you can leverage our technical skills and resources to develop a customized solution that meets your unique needs and helps you stay ahead of the curve. So why not take the first step and share your ideas with us today? We're ready and eager to help you take your business to the next level.
And don't Worry, we hold integritty at a high level and will sign an NDA with you, so your secrets are safe with us!